使用OpenSSL搭建简单一级CA
前言
之前写了一篇关于Nginx的客户端验证的文章,让大家使用XCA这个东西,没有讲用OpenSSL来建一个CA,故本文章来讲一讲。
本文章主要介绍搭建一个简单的一级CA,由根证书直接签发最终用户证书。
配置与签发
本次使用的配置文件如下:
[ ca ]
default_ca = CA_default
[ CA_default ]
# 一些目录配置
dir = .
certs = $dir/certs
crl_dir = $dir/crl
database = $dir/index.txt
new_certs_dir = $dir/newcerts
certificate = $dir/cacert.crt
serial = $dir/serial
crlnumber = $dir/crlnumber
crl = $dir/crl.crl
private_key = $dir/cakey.key
# x509证书扩展配置
x509_extensions = usr_cert
# 证书主题选项
name_opt = ca_default
cert_opt = ca_default
# 有效期
default_days = 730
# 默认crl列表更新时间
default_crl_days= 30
# 默认签名哈希算法
default_md = default
# 保持DN顺序
preserve = no
# 证书主题策略
policy = policy_match
# 不复制来自证书请求文件的扩展
copy_extensions = none
[ crl_info ]
# crl分发点,这个链接必须为URI且指向crl列表
URI.0 = http://ca.coat.jp/root/ca.crl
[ policy_match ]
# 主题均为可选
countryName = optional
stateOrProvinceName = optional
organizationName = optional
organizationalUnitName = optional
commonName = optional
emailAddress = optional
[ req ]
default_bits = 2048
default_keyfile = privkey.pem
# 要求填写的字段名DN
distinguished_name = req_distinguished_name
x509_extensions = v3_ca
string_mask = utf8only
[ req_distinguished_name ]
countryName = Country Name (2 letter code)
countryName_default = JP
countryName_min = 2
countryName_max = 2
stateOrProvinceName = State or Province Name (full name)
stateOrProvinceName_default = Simokitazawa
localityName = Locality Name (eg, city)
0.organizationName = Organization Name (eg, company)
0.organizationName_default = COAT Inc.
#1.organizationName = Second Organization Name (eg, company)
#1.organizationName_default = World Wide Web Pty Ltd
organizationalUnitName = Organizational Unit Name (eg, section)
commonName = Common Name (e.g. server FQDN or YOUR name)
commonName_default = COAT Email CA
commonName_max = 64
emailAddress = Email Address
emailAddress_max = 64
[ usr_cert ]
# 基本约束
basicConstraints=CA:FALSE
# 扩展用户用法,这里指定了证书的用途
# 如果你看了之前那片文章并使用了XCA,在它的选项卡中有这些选项,不填写为所有应用程序策略
# https://www.openssl.org/docs/manmaster/man5/x509v3_config.html
extendedKeyUsage = emailProtection,clientAuth
# 配置crl列表
crlDistributionPoints = @crl_info
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid,issuer
[ v3_ca ]
subjectKeyIdentifier=hash
authorityKeyIdentifier=keyid:always,issuer
basicConstraints = critical,CA:true
# 秘钥用法
keyUsage = cRLSign, keyCertSign
extendedKeyUsage = emailProtection,clientAuth
crlDistributionPoints = @crl_info
配置CA目录:
mkdir emailCA && cd emailCA
mkdir certs
mkdir crl
mkdir newcerts
echo "01" > serial
echo "01" > crlnumber
touch index.txt
首先生成根证书证书请求:
openssl req -new -config openssl.cnf -out ca.csr -keyout cakey.key
自签名根证书:
openssl ca -selfsign -config openssl.cnf -in ca.csr -out cacert.crt -extensions v3_ca
签发后长这样:
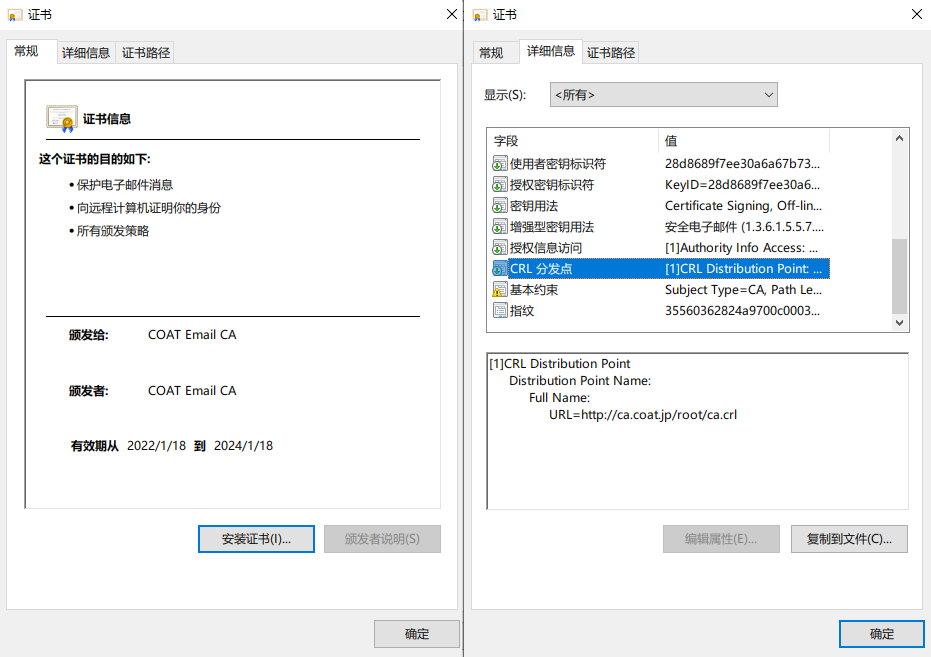
用户证书配置文件:
[ req ]
default_bits = 2048
encrypt_key = no
utf8 = yes
string_mask = utf8only
req_extensions = v3_req
prompt = yes
distinguished_name = distinguished_name
[distinguished_name]
emailAddress = Email Address
emailAddress_max = 64
[ v3_req ]
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
生成用户证书请求:
openssl req -new -config email.cnf -out certs/email.csr -keyout certs/email.key
签发用户证书请求:
openssl ca -config openssl.cnf -in certs/email.csr -out certs/email.crt -extensions usr_cert -days 365
签发后长这样:
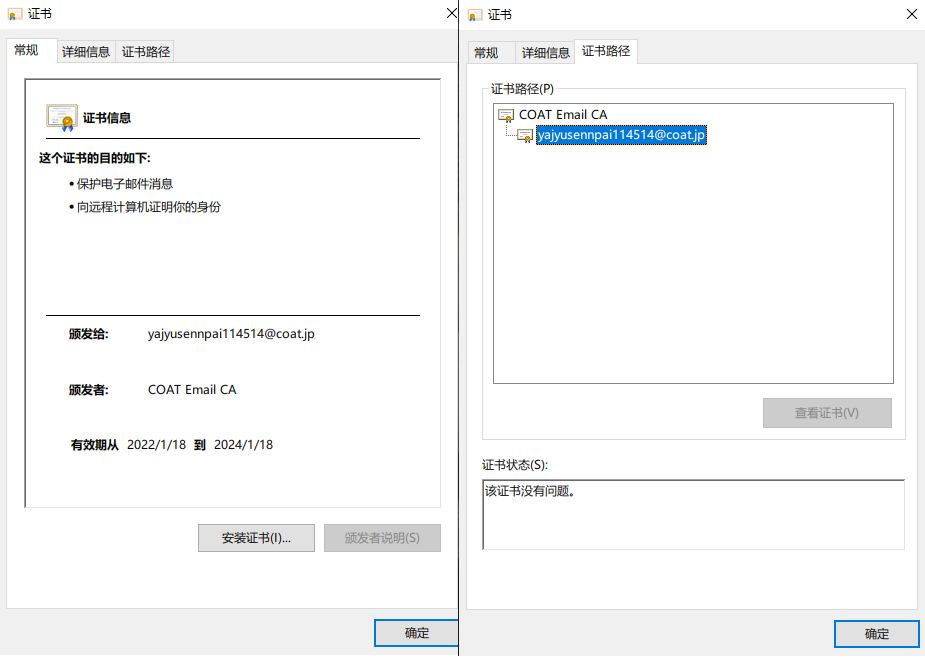
吊销证书:
openssl ca -config openssl.cnf -revoke certs/email.crt
生成crl列表:
openssl ca -config openssl.cnf -gencrl -out ca.crl
结尾
一级CA搭建较为简单,但并不常用,一般都是由根签发二级CA,再由二级CA签发给用户,这种方式方便不同用途的证书管理,同时防止CA被爆破导致签发的证书作废带来的影响。
在下一篇文章将讲述一个二级CA与OCSP服务器的搭建。