搭建STUN服务器
前言
STUN Server是一座灯塔,照亮通向你我之间的道路。本文在Alpine Linux上编译STUNTMAN来搭建STUN Server,简单够用。
安装
# 安装依赖
apk update
apk add openssl-dev boost-dev
# 下载&编译
wget https://www.stunprotocol.org/stunserver-1.2.16.tgz
tar xvf stunserver-1.2.16.tgz
cd stunserver
make
编译完成后有3个文件:
stunclient 客户端
stunserver 服务器
stuntestcode 单元测试
我们只关心服务器的使用,其他可使用--help来查看用法。
./stunserver
结果:
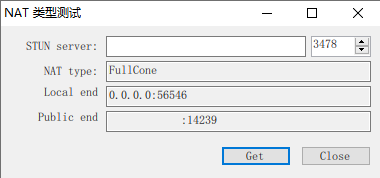
结尾
你可以选择更吼的STUN Server,比方说coturn,因为STUNTMAN到目前已经两年没更新了: